The term Zero Trust is appearing everywhere in the cybersecurity industry, and with good reason. Zero Trust is the new ABC of security – Assume nothing, Believe no-one, Check everything. It means that the security mechanisms that we use to protect our systems should not assume that a security decision made some time ago is valid. Rather, we should assume that any access request could be malicious.
The context for Zero Trust is the decision-making process that mediates access from a source or subject to a resource or object. The source or subject can be a person, a system, a serverless application or function, or an artificial intelligence. The resource or object can be data, a system, an application or function, or another artificial intelligence.
The concept of Zero Trust first emerged from Forrester in 2011, in a report by John Kindervag. The Forrester concept of Zero Trust introduced the notion that threats are present at all times, inside and outside the enterprise, so we must always defend against them. Since then, NIST has published guidance defining Zero Trust as an evolving set of cybersecurity paradigms that move defences from static, network-based perimeters to focus on users, assets, and resources. Microsoft points to the need for every access request to be fully authenticated, authorised, and encrypted before granting access. Crowdstrike suggests it means that all users, even those inside the organisation’s enterprise network, must be authenticated, authorised, and using a device that has a continuously validated security configuration and posture before being granted, or keeping, access to applications and data.
Four security mechanisms are recognised as necessary for a Zero Trust solution. The first is Just in Time Access (JITA), a mechanism used to provide the means to positively authenticate an entity request at the time the request is made, rather than assuming the request is authentic because of a token or certificate that was issued in the past. The second is Just Enough Access (JEA), to ensure that only those privileges needed to carry out the request are provided and only for the duration of the request. The third is Data-Centric Security, with tokenisation or encryption mechanisms used to desensitise data and reduce the data attack surface. And the fourth is a Dynamic Access Policy, continuously making policy adjustments using a rich source of environmental information so that access decisions adapt to dynamically changing subject rights and privileges and object sensitivities.
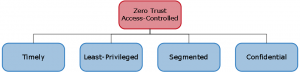
Zero Trust Access-Controlled is a special form of the Access-Controlled SABSA attribute that decomposes to Timely, Least-Privileged, Segmented, and Confidential. In addition, and in support of the enhanced security expected from Zero Trust, we need to include the attribute Trustworthy. The SABSA Institute is working on a complete design pattern to support this interpretation of Zero Trust.
Malcolm Shore
Chief Security Architect
Malcolm combines a wealth of practical experience including security leadership roles across Australia & New Zealand, specialising in telecommunications, with an academic skill set comprising training development, research and publication.
